
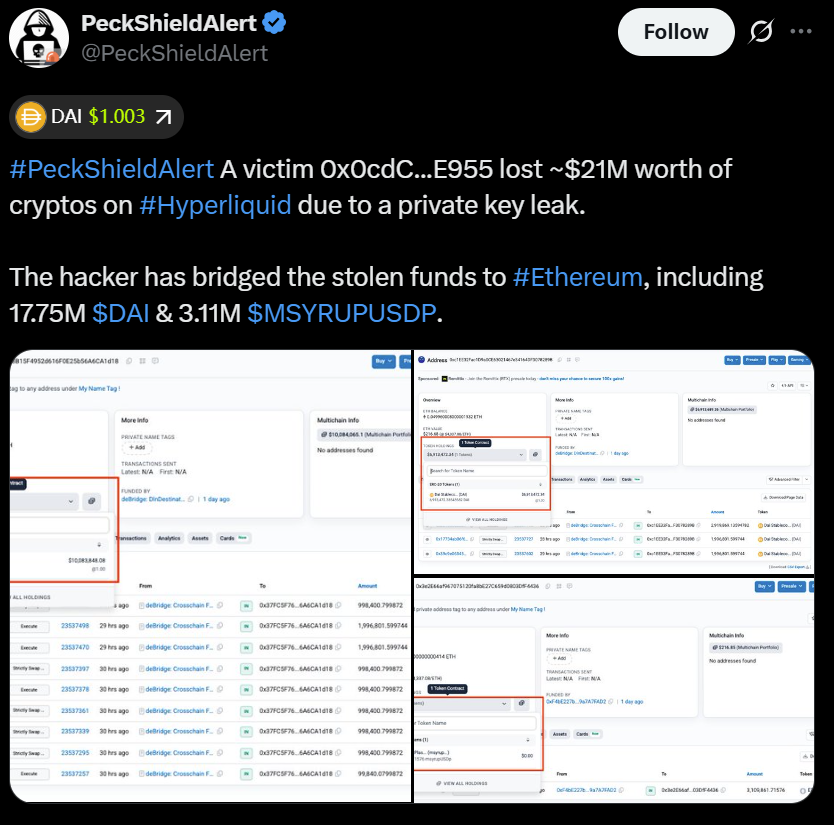
On Thursday, an individual trading on the decentralized platform Hyperliquid lost approximately $21 million due to a leak of a private key, which permitted an exploit connected to the platform’s Hyperdrive lending protocol.
According to PeckShield, a blockchain security firm, the hacker targeted 17.75 million DAI and 3.11 million SyrupUSDC, a synthetic variant of the USDC stablecoin utilized within Hyperdrive. The stolen funds were then transferred to Ethereum.
PeckShield has yet to verify how the private key became compromised.
 Crypto Exploit Image
Source: PeckShieldAlert
Crypto Exploit Image
Source: PeckShieldAlert
This incident occurs during a period of rapid growth for Hyperliquid, which has gained attention due to its rewards program aimed at enhancing liquidity and user engagement. Recently, it completed a significant airdrop distribution to over 94,000 addresses. In just a week, the platform has managed over $3.5 billion in trading volume, according to data from DefiLlama.
With decentralized exchanges (DEXs) seeing renewed interest, this event raises a critical question: How can users secure themselves in a self-custodial ecosystem based on smart contracts?
Staying Safe as a Trader
Although the cause of the exploit is under examination, security experts stress that users of decentralized exchanges should adopt various precautions to protect their assets. DEXs like Hyperliquid provide traders with complete control over their crypto holdings, which also entails full responsibility for their security. It is wise to maintain a “hot” wallet for active trading and a “cold” wallet for long-term storage, keeping the majority of funds offline and out of reach from online threats.
Only a minimal fraction of a trader’s total assets should be stored in wallets connected to DEXs to mitigate potential losses in case of a private key breach or harmful smart contracts.
Furthermore, Hyperliquid users should never disclose their private keys or seed phrases, even during API wallet configurations. Hyperliquid’s documentation notably warns: “Do not share your private key with anyone.” Users should also be vigilant against fake “authorization” pages or support asks on platforms like Telegram or Discord, which often disguise themselves as official personnel to misappropriate credentials.
 Security Data
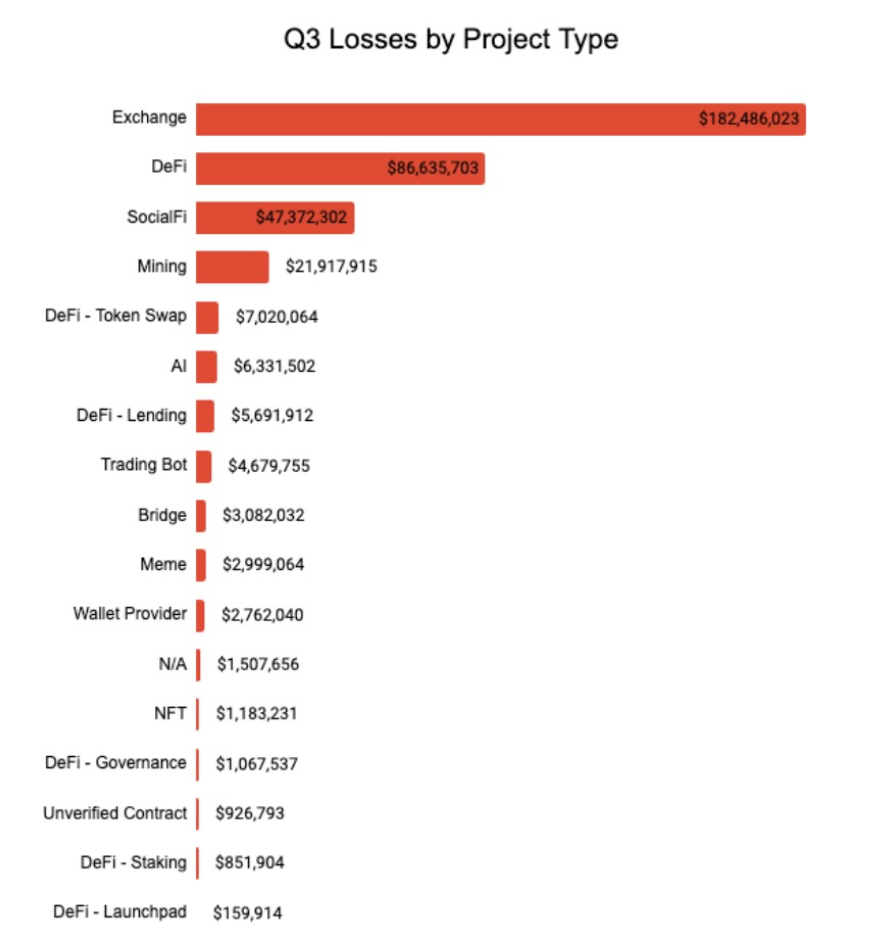
As of Q3 2025, crypto exchanges and DeFi protocols were leading attack vectors for hacks and exploits. Source: CertiK
Security Data
As of Q3 2025, crypto exchanges and DeFi protocols were leading attack vectors for hacks and exploits. Source: CertiK
Following the Hyperliquid exploit, the MEXC crypto exchange advised users to “check positions and approvals on a block explorer,” reminding that troubles often arise when users allow too many permissions to DeFi applications. Security specialists recommend routinely reviewing and rescinding unnecessary permissions using tools like Etherscan’s Token Approvals or similar on-chain management services.



