
Understanding EtherHiding: A New Threat in Crypto Malware
North Korean hackers implement EtherHiding, a technique embedding malware in smart contracts to steal sensitive data.
Introduction
“EtherHiding” operates in a dual-phase approach by infiltrating a website to integrate malicious code secured in a smart contract.
Methodology
According to Google’s Threat Intelligence Group, North Korean hackers utilize this new tactic, EtherHiding, which surfaced in 2023. This method is often combined with social engineering strategies, getting victims through fabricated job offers and prestigious interviews, guiding them to harmful links or websites.
Hackers gain access to a genuine website using a Loader Script, implanting JavaScript code that activates a distinct malicious program within a smart contract meant to seize funds and confidential information when the target interacts with the tainted site.
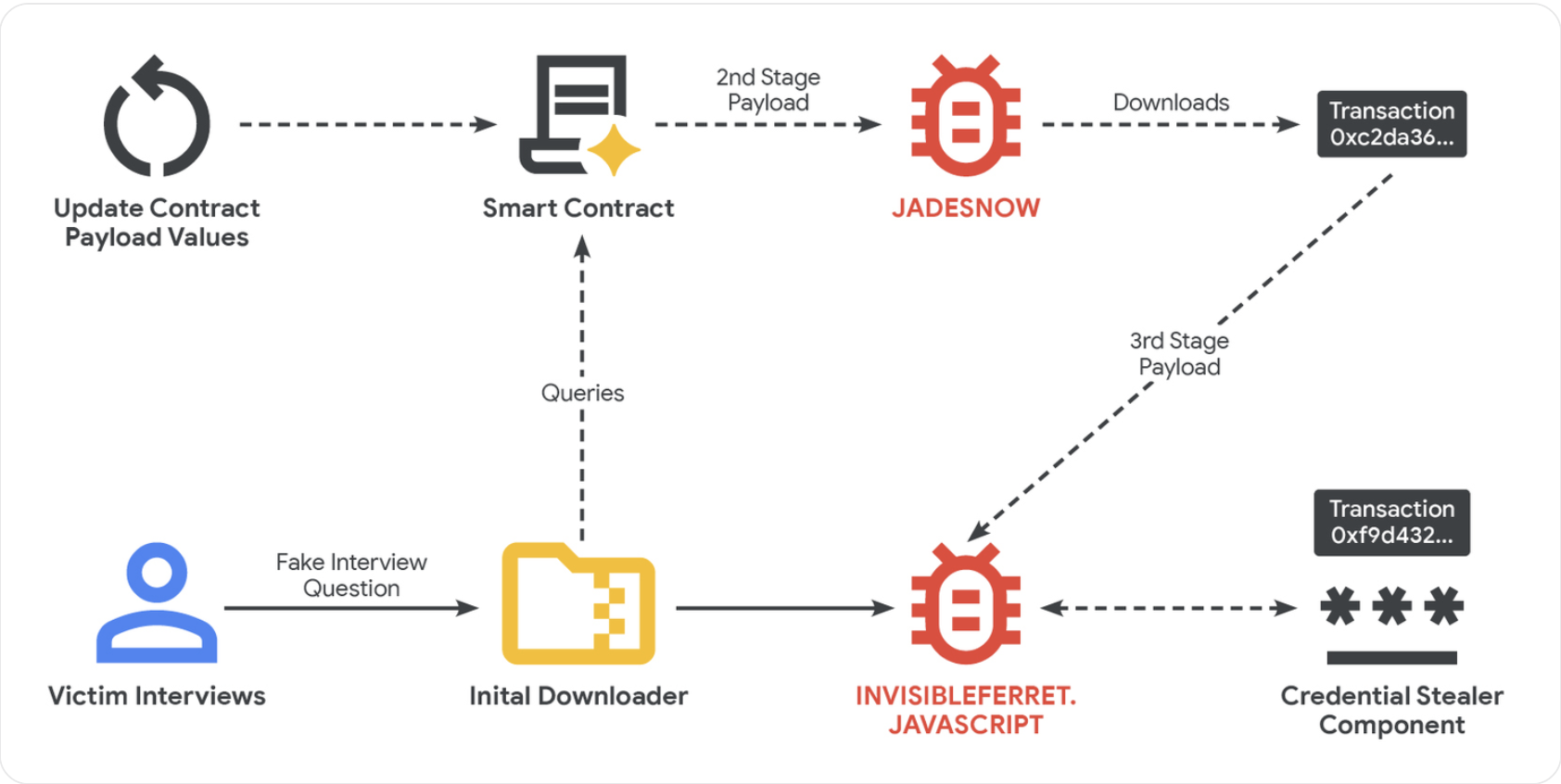 Illustration of EtherHiding Technique
Simplified illustration of how the “EtherHiding” hack works. Source: Google Cloud
Illustration of EtherHiding Technique
Simplified illustration of how the “EtherHiding” hack works. Source: Google Cloud
The affected website interacts with the blockchain network using a “read-only” function, avoiding actual transactions on the ledger. This circumvention allows hackers to elude detection while minimizing fees, according to Google researchers.
Community Awareness
The report underscores the critical necessity for the crypto community to remain alert against prevalent scams and hacking attempts from malicious entities aimed at stealing funds and sensitive data.
Recognizing the Threat
The malicious actors set up fictitious companies and recruitment platforms to target software and cryptocurrency developers via phony job offers. After an initial engagement, the dialogue shifts to messaging applications like Discord or Telegram, coercing victims into testing or coding tasks.
“The core of the attack occurs during a technical assessment phase,” explained Google Threat Intelligence.
During this stage, victims usually download harmful files from online repositories, such as GitHub, that contain the malicious payload. Alternatively, attackers may entice victims into video calls, where a false error prompts them to download a fix that also harbors malicious software.
Upon installation, the secondary malware, known as JADESNOW, operates to extract sensitive information.
In some high-stakes instances, a third phase is implemented, granting attackers extended access to compromised systems and networks, as Google has warned.


