
Understanding EtherHiding: Google Uncovers Cryptocurrency-Theft Malware in Smart Contracts
A new malware technique, EtherHiding, has been identified by Google's Threat Intelligence, utilizing smart contracts to compromise users' crypto accounts.
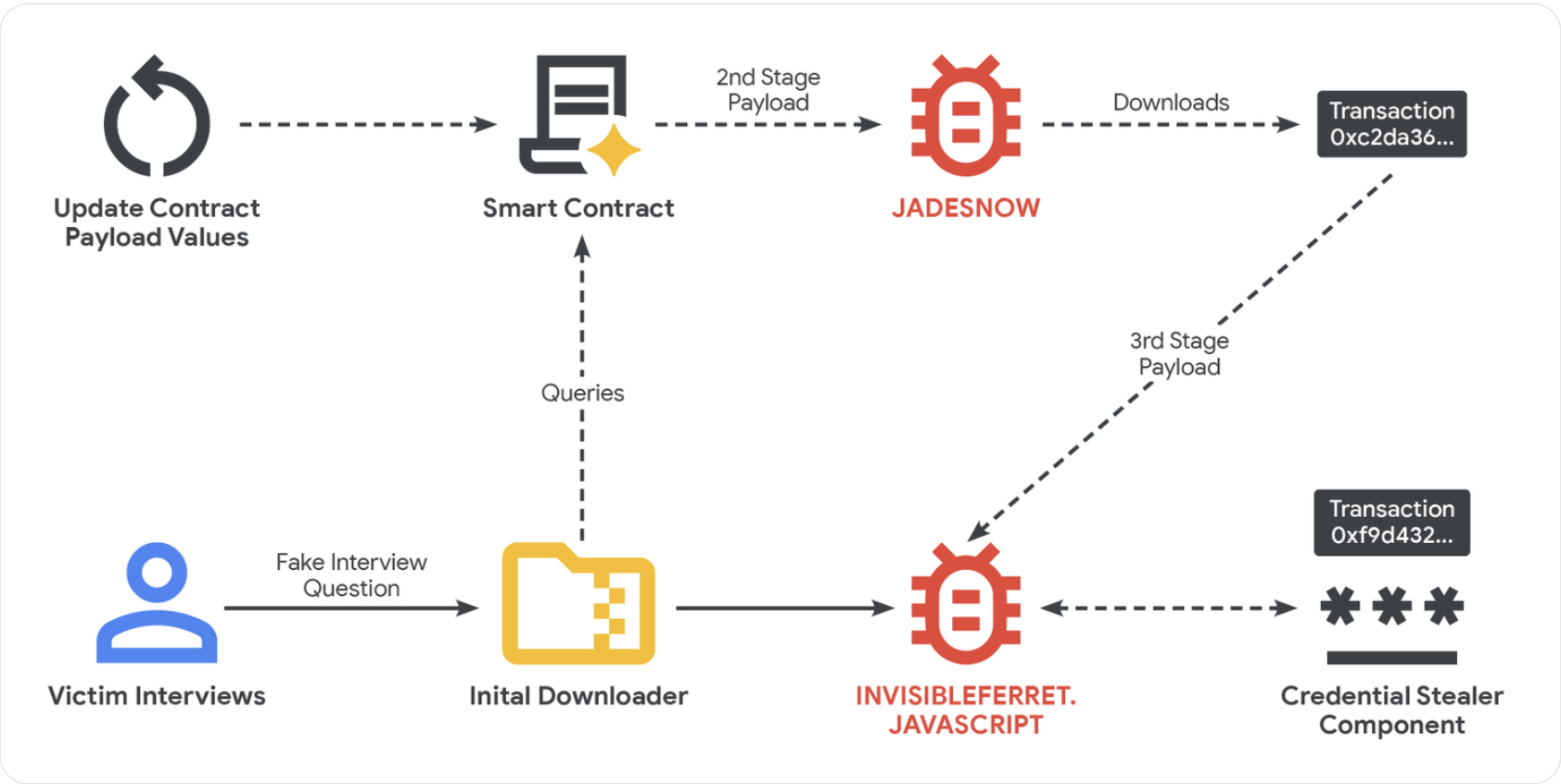
The malicious technique known as EtherHiding is leveraging two stages to infiltrate websites, allowing the installation of harmful code within smart contracts.
According to Google’s Threat Intelligence Group, North Korean hackers have begun embedding malware in public blockchain smart contracts to steal sensitive data. This technique surfaced in 2023 and involves using social engineering tactics to deceive victims through fake job offers that lead them to compromised sites.
Once hackers gain control of a legitimate web address via a Loader Script, they insert malicious JavaScript that activates a secondary piece of harmful code embedded in a smart contract. This code is designed to extract both funds and personal information once a user engages with the tainted site.
“The compromised website will communicate with the blockchain network using a ‘read-only’ function that avoids creating any transactions on the ledger, thus helping to bypass detection and reduce transaction costs,” according to Google’s findings.
 EtherHiding Hack Illustration
Source: Google Cloud
EtherHiding Hack Illustration
Source: Google Cloud
The report emphasizes the importance of vigilance within the cryptocurrency community to protect users from common scams and cyber attacks aimed at stealing crucial information.
Identifying the Threats
The attackers create fake companies, agencies, and profiles to lure in software developers, often moving their conversations to messaging platforms like Discord or Telegram. During the evaluation phase of the fake employment, victims may be instructed to download malicious files from online repositories like GitHub.
Throughout these schemes, attackers may initiate video calls with the victim, displaying fabricated error messages urging them to download patches that in reality contain harmful software. Once this software is installed, JavaScript-based malware, known as JADESNOW, executes to siphon sensitive data.
At times, a third stage may follow for significant targets, ensuring the assailants can maintain long-term access to the compromised system and any connected networks. Google warns the community of the potential dangers of these elaborate schemes.


