
Understanding EtherHiding: Google's Warning on Crypto-Theft Malware
Google's Threat Intelligence Group reveals a dangerous method called EtherHiding used by North Korean hackers to steal cryptocurrency through smart contracts.
Google’s Threat Intelligence Group has reported a novel approach to cybercrime known as EtherHiding, utilized by North Korean hackers to infiltrate computers and extract cryptocurrencies through malicious code hidden in smart contracts on public blockchains.
This technique, which surfaced in 2023, often employs social engineering tactics by enticing victims with fake job offers and connecting them to malicious sites or links, as detailed by Google.
The perpetrators exploit legitimate websites by inserting a Loader Script that activates harmful JavaScript, which in turn triggers additional malicious components within a smart contract aimed at pilfering funds and data once users engage with the tainted site.
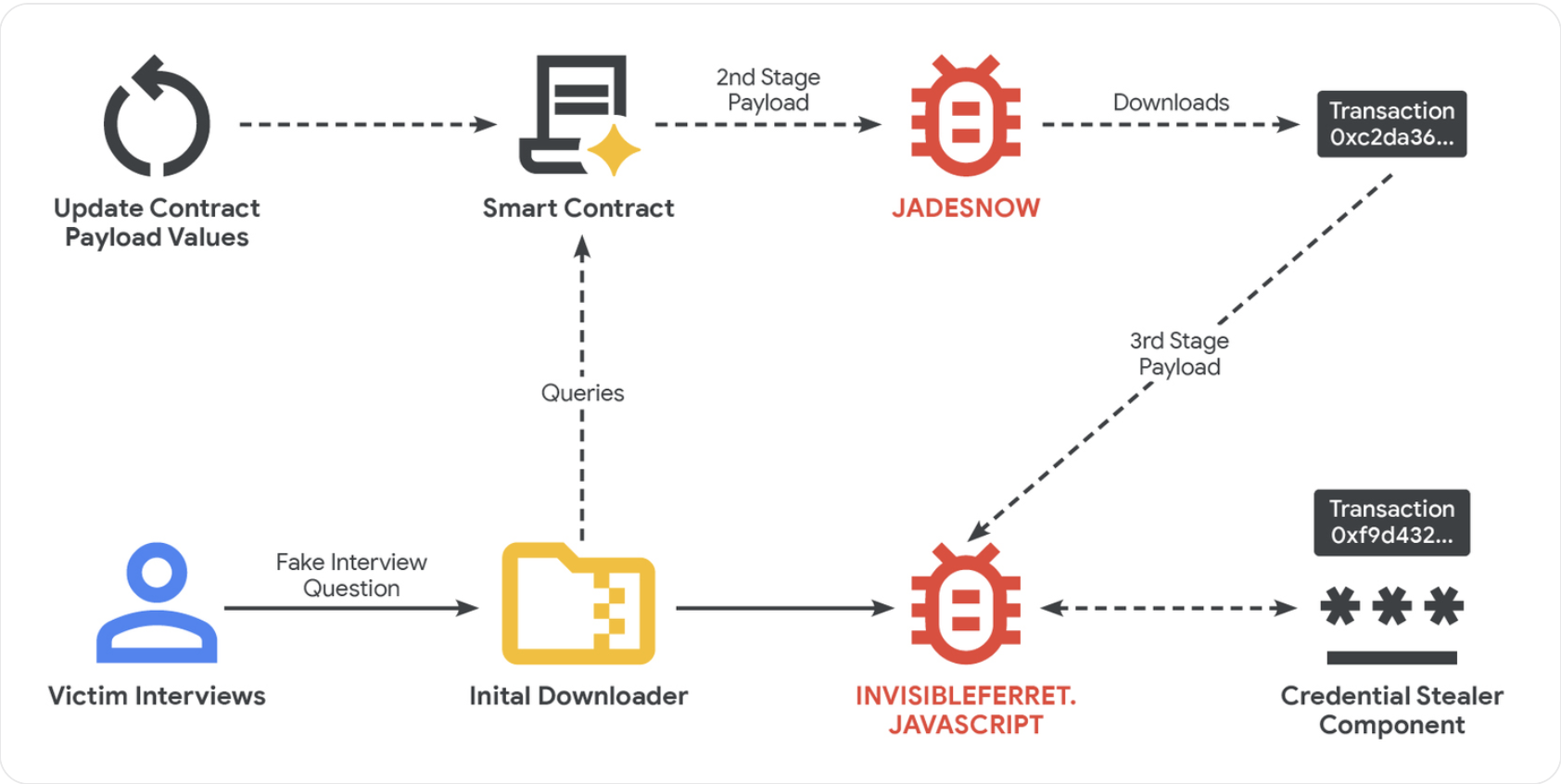 Illustration of EtherHiding Hack
Simplified illustration of how the “EtherHiding” hack works. Source: Google Cloud
Illustration of EtherHiding Hack
Simplified illustration of how the “EtherHiding” hack works. Source: Google Cloud
The infected site communicates with the blockchain using a read-only function, avoiding any detectable transactions on the ledger, which helps the attackers escape notice and reduce transaction costs, as noted by researchers at Google.
The report emphasizes the necessity for caution within the crypto community to protect individuals from the scams and attacks frequently utilized by these threat actors aiming to embezzle both funds and sensitive information.
Warning Signs: Deciphering North Korea’s Social Engineering Initiatives
According to Google, the threat actors may establish fake companies and recruitment agencies targeting developers with deceptive job offers. Post initial contact, they often transition discussions to platforms like Discord or Telegram, directing victims to perform employment assessments or coding tests.
“The core of the attack unfolds during the technical evaluation phase,” Google’s Threat Intelligence Division affirmed. Here, prompts for downloading harmful files from online repositories like GitHub become prevalent, where the harmful payload is hidden.
In other instances, attackers may engage victims via a video call, exhibiting a fabricated error message that compels them to download a supposed patch to rectify the issue, which also contains harmful code.
Once the malware is embedded in a device, a second-stage JavaScript malware known as JADESNOW activates, aimed at extracting sensitive data.
Sometimes, a third phase is launched, especially targeting high-value individuals, providing criminals with prolonged access to both the compromised device and its associated networks, Google cautioned.


