
What is EtherHiding?
The technique dubbed EtherHiding is reportedly leveraged by North Korean hackers to integrate malware that specifically targets cryptocurrency and sensitive data. It operates through a two-phase deployment mechanism, where a legitimate website is compromised, facilitating a connection to harmful JavaScript included in a smart contract.
According to Google’s Threat Intelligence Group, this method emerged in 2023 and is usually paired with social engineering strategies. Hackers utilize methods such as sending fraudulent job offers and coordinating high-profile interviews, leading individuals to malicious links.
The Mechanism of EtherHiding
Typically, attackers gain access to an authentic website using a Loader Script, which inserts malicious JavaScript. This triggers additional code within the smart contract, aimed at pilfering funds and sensitive information once a victim interacts with the compromised site.
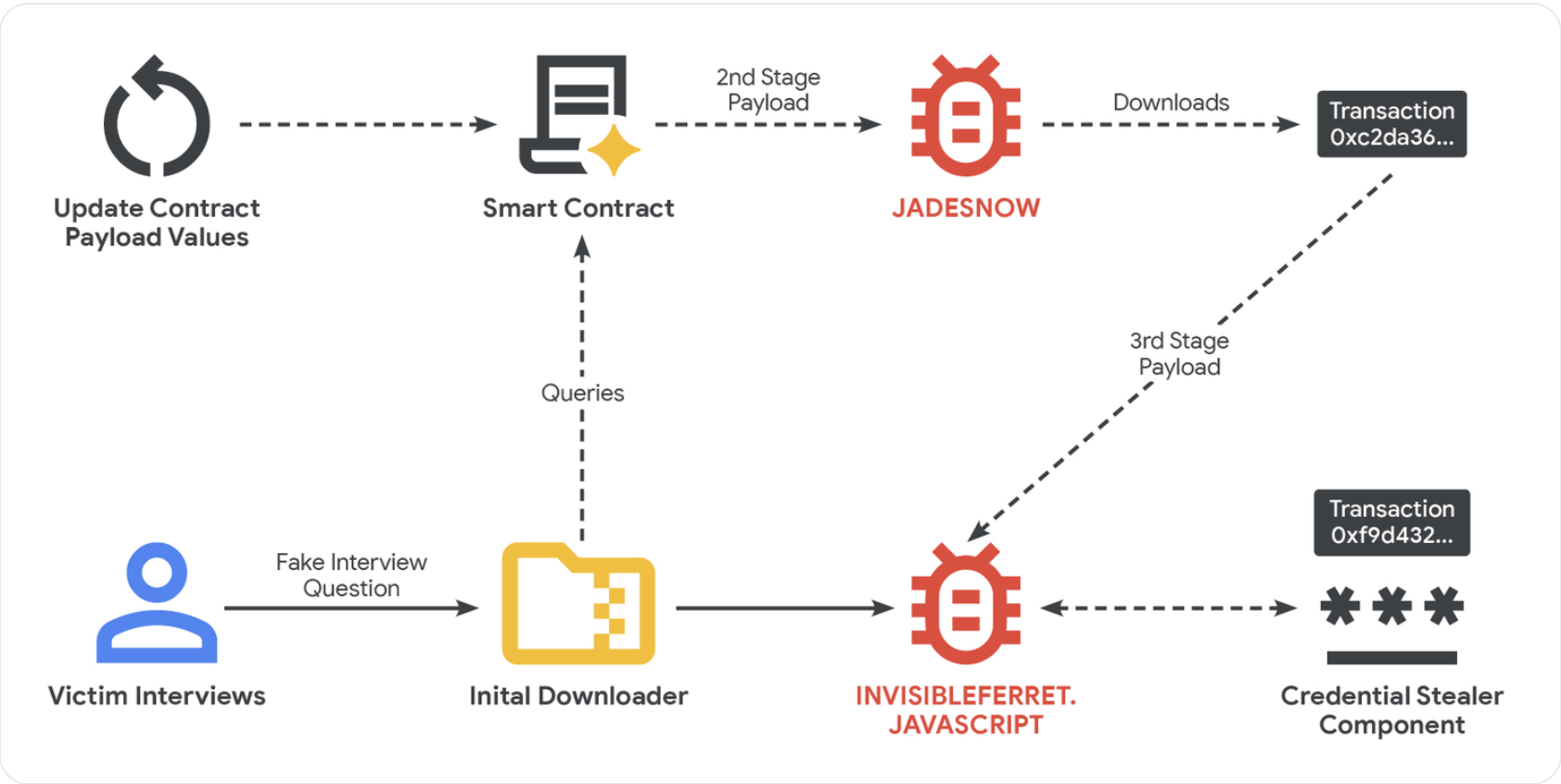 Simplified illustration of how the “EtherHiding” hack works. Source: Google Cloud
Simplified illustration of how the “EtherHiding” hack works. Source: Google Cloud
The compromised site communicates via a read-only function, allowing hackers to navigate around detection and limit transaction costs, as noted by the researchers.
The Need for Vigilance
This report has raised alarms within the crypto community, underscoring the importance of protecting users from scams and hacks, which are commonly used by malicious entities trying to steal funds and valuable information.
Recognizing the Signs
Google’s insights point to a pattern of fake companies and recruitment agencies targeting software and cryptocurrency developers through fraudulent job offers.
After approaching prospects, attackers frequently shift discussions to platforms like Discord or Telegram and request potential victims to complete tests, often asking them to download malicious files hosted on sites like GitHub, where the malware resides.
Further techniques include luring individuals into video calls and displaying fabricated error messages to induce them into downloading harmful patches that harbor the malware.
Once installed, secondary malware known as JADESNOW can extract confidential data, and in certain situations, a third stage allows persistent access to compromised systems.
Conclusion
This evolving method demands heightened awareness and precaution among cryptocurrency users to fend off potential cybersecurity threats.


