
Top Tactics of North Korean Hackers: Spear Phishing Explained
AhnLab warns that artificial intelligence will amplify the sophistication of cyber attacks in 2026, making spear phishing a leading concern for cybersecurity.
Spear Phishing: A Focus of North Korean Cyber Attacks
AhnLab identifies spear phishing attacks as the primary method utilized by North Korean hackers, specifically the Lazarus Group, over the previous year. This method has been noted for its effectiveness in deceiving victims through spoofed emails posing as legitimate communications like lecture invitations or interview offers, making it a significant concern as we approach 2026.
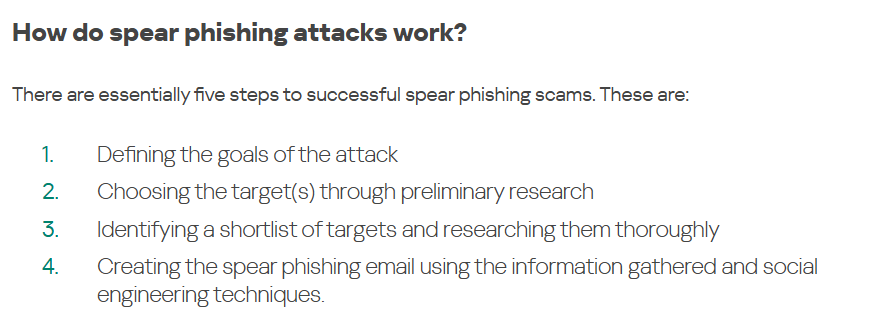 Spear Phishing
Figure: Spear phishing attacks demand advanced preparation from the attackers. Source: Kaspersky
Spear Phishing
Figure: Spear phishing attacks demand advanced preparation from the attackers. Source: Kaspersky
The Lazarus Group is attributed as the leading suspect in numerous cyber attacks, impacting various sectors including cryptocurrency. They are implicated in notable breaches like the $1.4 billion Bybit hack and the $30 million exploit involving the South Korean exchange Upbit.
Protective Measures Against Spear Phishing
To defend against spear phishing, AhnLab recommends several strategies:
- Use a VPN to secure your online actions.
- Be cautious about revealing personal information online.
- Verify email sources through alternate channels.
- Enable multi-factor or biometric authentication wherever feasible.
The importance of a “multi-layered defense” is emphasized as essential for organizations to mitigate risks, which includes regular security audits, software updates, and staff education.
The Role of AI in Future Cyber Threats
Looking ahead to 2026, AhnLab raises alarms about the growing use of AI, which could enhance the capability of cyber criminals, making spear phishing attacks even more complex. AI may enable bad actors to create deceptive emails and websites that are increasingly challenging to differentiate from legitimate sources.
“With the rising utilization of AI models, deepfake attacks are likely to progress to a point where it’s hard for victims to recognize them. Vigilance is crucial to safeguard data from leaks.”
In conclusion, maintaining updated security measures and being vigilant to protect against social engineering attacks is more critical than ever.
